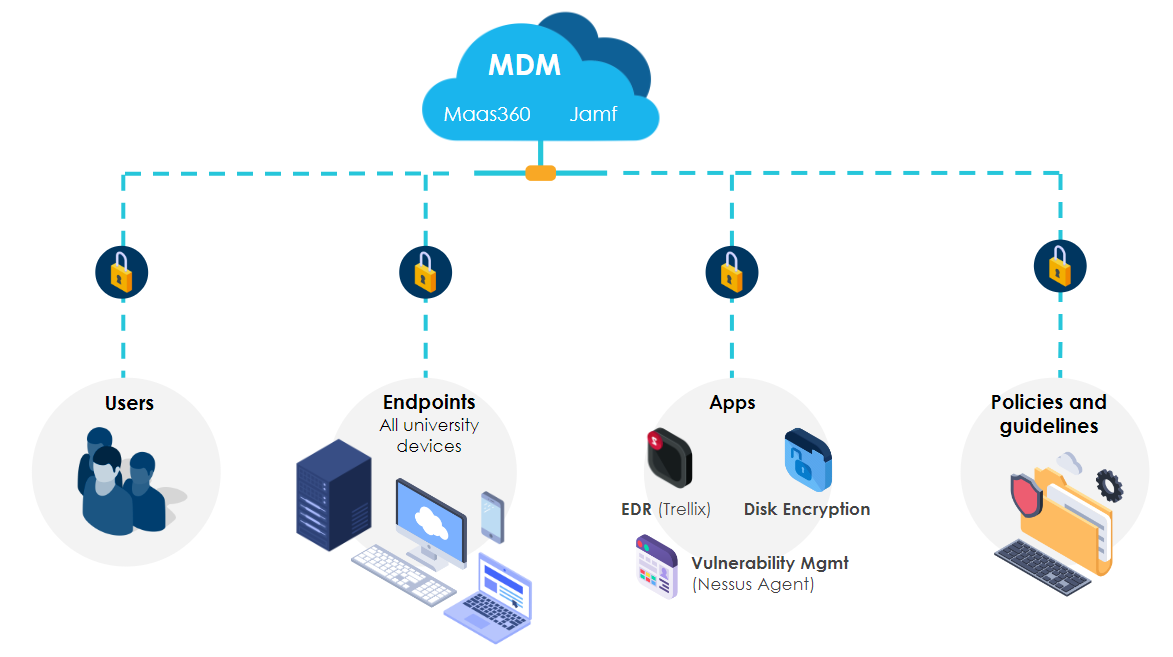
Device security is a core component of the new UC systemwide cybersecurity mandate. In order to meet new requirements, UCSB must deploy Endpoint Detection and Response (EDR) to all University-owned devices.
In cybersecurity, devices are considered “endpoints” that connect to a network. All endpoints are potential entry points for security threats. EDR software specializes in detecting and responding to endpoint-level threats. UCSB is rolling out an MDM tool in order to manage the installation and updating of EDR, malware protection and disk encryption software.
The Security Operations Center (SOC) already manages an EDR tool called Trellix and a malware protection program: Nessus Agent. Approximately 66% of campus devices / endpoints currently use these tools. The UCOP mandate requires 100% compliance.
Virtual webinar
On Nov. 7, 2024 we hosted a virtual Device Security webinar. Join Shea Lovan, Chief Technology Officer and Jackson Muhirwe, Director of Information Assurance and Chief Information Security Officer as they discuss upcoming cybersecurity tools for UCSB owned devices with Manny Cintron, Director of Workplace Technology Services and Ben Price, Associate CIO, Administrative Services.
Frequently Asked Questions
Review our FAQs to learn more about the project, including technical details on scope and equipment.
IT Security
The University takes steps to ensure the security of our infrastructure and systems, but cybersecurity is a shared responsibility, and everyone can take a few simple steps to make the Internet more secure!
Contact Us
Have questions or concerns about Secure UCSB?
Send us a message at secure-ucsb@it.ucsb.edu